Comprehensive guide to vendor risk management (VRM)
Strengthen vendor risk management (VRM) with modern enterprise content management (ECM) systems. Enhance assessments, automate workflows and ensure compliance.
Strengthen vendor risk management (VRM) with modern enterprise content management (ECM) systems. Enhance assessments, automate workflows and ensure compliance.

Organizations rely on third-party vendors, which can create vulnerabilities and challenges in terms of control, compliance and visibility into operations. As a result, vendor risk management (VRM) is more important than ever. This guide offers actionable insights to enhance your vendor relationship risk management strategies.
Vendor relationship management (VRM) is the process of identifying, evaluating and mitigating the potential risks associated with third-party vendors. It involves continuous monitoring and assessment to ensure a desired level of security and operational performance.
Visibility, control and compliance in vendor relationships can help companies prevent data breaches, support operational continuity and meet regulatory requirements. Without these elements, companies risk facing significant financial losses, reputational damage and legal repercussions.
Outsourcing tasks to vendors introduces vulnerabilities as companies rely on a vendor's security practices when they share data or access to external systems. Alarmingly, 98% of organizations have a relationship with at least one third party that has experienced a breach in the last two years.
Robust VRM practices that optimize vendor selection, set standards for approved vendors and ensure consistent monitoring can significantly reduce both risks and vulnerabilities, thereby enhancing business resilience. Specifically, VRM helps safeguard sensitive data and enhance accountability within vendor relationships.

Explore Gartner’s analysis of 15 vendors in the document management space, and see why Hyland was named a Challenger with strengths in our scalability, open source and industry-specific capabilities.
A VRM assessment involves several steps to make certain that all potential vulnerabilities are addressed and managed effectively. Consider the following structured approach when working with your own company's vendors:
List all potential vendors and prioritize them based on their risk profiles and importance to operations. Categorizing vendors in this way can help in allocating resources to manage high-risk vendors later, thereby enforcing security and business continuity.
Conduct background checks, financial health assessments and compliance reviews to confirm that each vendor under consideration has a solid reputation and can meet your organization’s standards. This step is crucial to verify their credibility and to prevent any potential risks before formalizing agreements.
Choose a well-established risk assessment framework, such as ISO 27001 or NIST SP 800-53, to provide structured guidelines for evaluating vendor risk. These frameworks help standardize the assessment process, providing consistency and thoroughness in identifying potential vulnerabilities.
Create detailed questionnaires to assess the security controls, compliance status and operational processes of each vendor. These questionnaires should be tailored to the specific risks associated with the types of services each vendor provides. The aim being to provide a comprehensive evaluation of all relevant risk factors.
Evaluate the responses from the risk questionnaires to identify potential vulnerabilities and areas of concern within each vendor's operations. Assign risk scores based on the likelihood of these risks occurring and their potential impact on your organization.
Define clear terms, including service-level agreements (SLAs) and risk mitigation clauses, during contract negotiations. This provides clear performance expectations and safeguards to protect against identified risks.
Implement a structured onboarding process with initial risk assessments and monitoring protocols. This helps vendors meet your organization’s compliance and security standards from the outset, enabling early identification of potential risks.
Continuous monitoring guarantees that your organization maintains an up-to-date understanding of each vendor's compliance status and operational performance.
Utilize automated tools for real-time tracking of vendor performance and compliance to gain immediate insights into potential risks. Regularly review and reassess vendors to identify and address any new risks that may arise over time.
Develop and implement plans to address high-risk areas. This includes remediation steps to resolve identified issues and contingency planning to prepare for potential disruptions.
By proactively addressing these high-risk areas, your organization can maintain operational continuity and minimize the impact of any vendor-related incidents.
When offboarding a vendor, uphold a secure and compliant termination process by retrieving any sensitive company data and removing all access credentials. Conduct a final compliance review to confirm that all contractual obligations have been met and document the offboarding process for future audits.
A risk matrix can help in the evaluation of vendor risk. These graphical tools — depicted as a grid, with one axis representing likelihood and the other depicting impact — help define risk levels by evaluating both the probability and outcome of a given event. Including the numbers of vendors in each category is also essential.
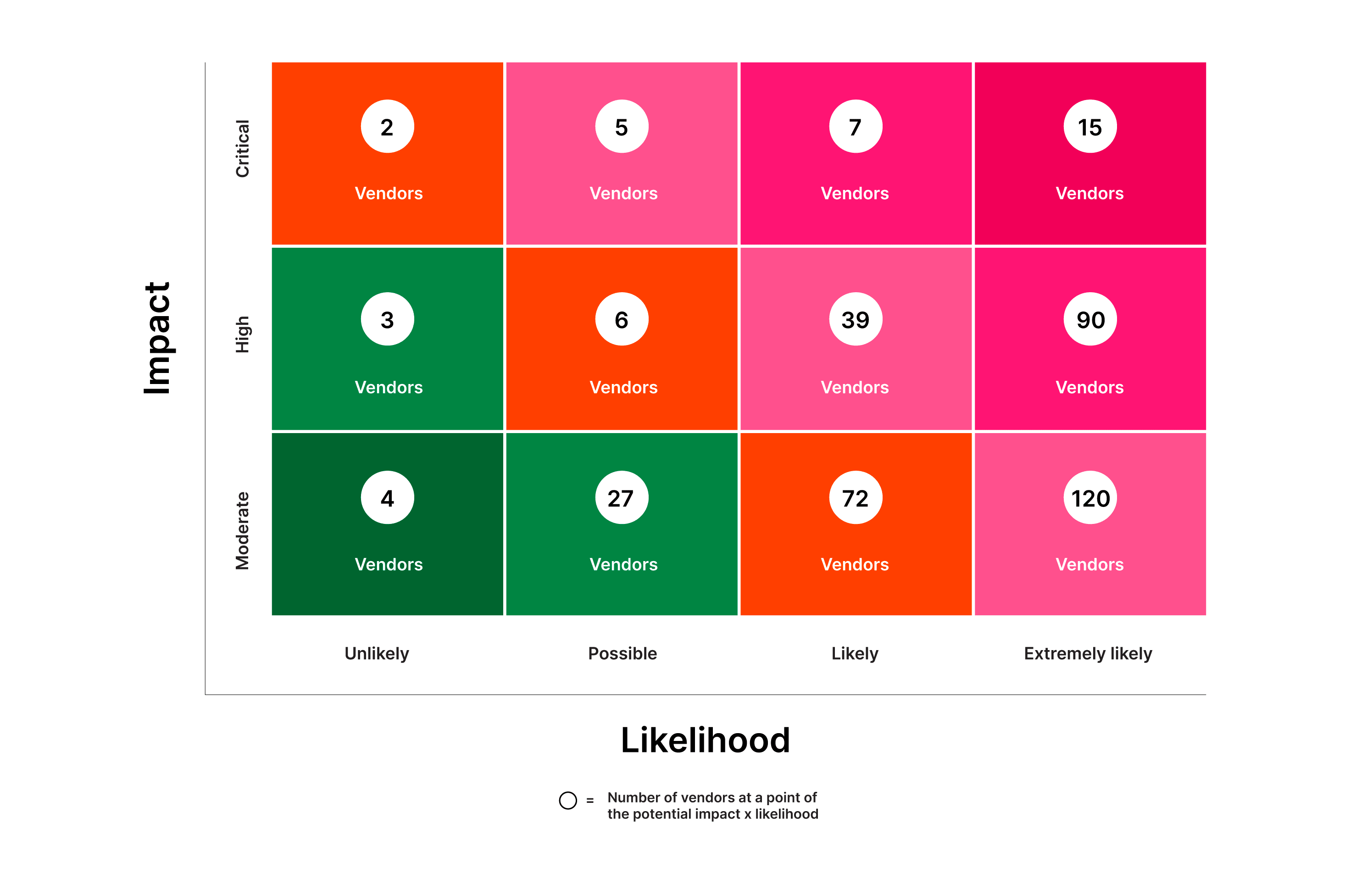
This visual representation aids in identifying high-risk areas that require immediate attention. It allows for the efficient allocation of resources to decrease those risks, thus enhancing the overall effectiveness of the VRM process.
Areas within the risk matrix include:
The risk matrix is an invaluable tool in VRM because it provides a clear and unique representation of risks — beyond what's possible with more simplistic methods. It helps organizations prioritize their risk mitigation efforts and make better strategic decisions, making sure resources are allocated to the most critical areas.
The risk matrix is vital to a structured, comprehensive VRM strategy. Clear communication among stakeholders and efficient resource allocation foster transparency and assures that critical risks receive the attention and effort they require.
Vendor risks vary widely, each presenting unique challenges. Understanding and addressing these specific issues are essential for effective VRM:
Vendor risks can be effectively managed by implementing comprehensive risk assessments and continuous monitoring to avoid disruptions and even crises. Here are some strategies for managing vendor risks:
Artificial intelligence (AI) and automation can significantly enhance VRM processes by improving risk detection accuracy and enabling continuous monitoring of vendors, thus aiding in informed decision-making. These technologies assist in:
AI can automate otherwise manual processes — for example, it can automate the distribution and collection of risk questionnaires and reduce manual follow-ups. AI platforms can continuously monitor vendor activities and generate real-time reports, eliminating manual data compilation and reducing errors.
AI algorithms can analyze large datasets to predict potential risks accurately, identifying patterns and correlations. Since AI-powered platforms can process vast amounts of vendor data, companies can easily cross-reference with external sources to provide more comprehensive assessments.
AI speeds up vendor onboarding by automating credential verification and compliance checks, integrating vendor information seamlessly. Continuous risk tracking provides real-time monitoring of vendor performance and compliance, addressing emerging risks promptly.
Through intelligent document processing, AI-powered platforms can automate the capture, classification and extraction of data from vendor documents to reduce manual handling. Through content capture, they can extract critical information from contracts and compliance documents, providing immediate insights.
AI-powered platforms send real-time notifications to keep stakeholders informed of changes in vendor risk profiles. Collaboration tools facilitate communication between internal teams and vendors, improving transparency and issue resolution.

Modern enterprise content management (ECM) systems support VRM through the seamless integration of vendor data. These systems offer robust tools for compliance tracking, document automation and risk assessment, with features like:

Hyland offers a suite of modern content management platforms, each tailored to revolutionize your workflows and enhance productivity. Discover a new perspective on enterprise content management with Hyland and redefine the way you handle content, so you can make faster, better business decisions.
The need for comprehensive and automated VRM solutions is clear: 50% of organizations have indirect relationships with at least 200 fourth parties that have had breaches in the last two years.
Integrating ECM systems into VRM processes provides the advantages companies need with these challenges in mind. By improving organization, enhancing compliance tracking, automating workflows and optimizing document processing, companies can be confident as they expand their use of third-party vendors.

Discover how VRM optimizes supply chains, controls costs and fosters innovation, with Hyland’s ECM solutions.

Explore the essentials of ECM, its benefits and how it transforms content management to enhance efficiency and compliance in your organization.

Get the basics about the opportunities for infusing artificial intelligence into your content management strategy.

Discover actionable insights to enhance financial health and operational efficiency through effective cost management strategies.