How ECM systems fortify digital security
Discover how investing in modern enterprise content management (ECM) systems can secure your organization’s content today and ensure long-term business success.
Discover how investing in modern enterprise content management (ECM) systems can secure your organization’s content today and ensure long-term business success.

Content management system (CMS) security refers to the practices, protocols and technologies designed to protect digital content.
This includes safeguarding documents, images, videos and other digital assets against unauthorized access, data breaches and other threats.
Effective CMS security ensures content remains accurate, reliable and available only to those with the appropriate permissions, providing:

Discover how Hyland’s security-first culture builds customer trust and delivers products and services that meet the highest industry standards.
Content security threats include cyberattacks and various other challenges. Understanding these threats is essential for developing effective strategies to prevent them. Key areas include:
One of the most significant threats to content security comprises:
Leaks and stolen data can cause the loss of sensitive information, regulatory fines and damage to an organization’s reputation. Common causes include:
This can jeopardize vital information and operational continuity. It can occur due to:
The most challenging threats to detect and prevent are insider threats because they involve trusted individuals with legitimate access to systems and data. They can originate from:

ECM systems offer features and functionalities to protect sensitive information and ensure compliance with regulatory requirements. These include:
Granular role-based access controls (RBAC) limit users to only the information necessary for their job roles. Whether editing or just viewing, permissions can be inherited from containing folders or individually set based on business or security needs.
Multifactor authentication (MFA) adds extra security by requiring multiple forms of identification. This can include a password, authentication via smartphone apps using single-use codes, PIN or even biometrics.
Virtual private networks (VPNs) and firewalls provide secure, encrypted connections or ‘tunnels’ between the user and the ECM system, preventing external access.
Centralized data storage with stringent access policies ensures that content is stored securely.
Encryption protects data at rest (stored on a server) and in transit (being transmitted over a network), ensuring it remains unreadable if intercepted.
Audit trails track all document interactions, providing transparency and accountability to maintain data integrity and aid incident investigations.
ECM systems are designed to help organizations comply with regulatory requirements like GDPR, HIPAA and SOX, with automated compliance reporting capabilities.
This unburdens IT and compliance teams, helping organizations identify and address security and regulatory issues promptly.
Automated workflows help ensure reviews and approvals of business processes are streamlined. This reduces the need for manual intervention, improving efficiency and reducing errors.
ECM systems can manage document retention lifecycles according to regulations and standards, requiring minimal human intervention beyond initial setup and updates.
Regular security audits identify and fix system vulnerabilities to ensure the system's defenses remain robust, current and protected against emerging threats.
Incident response plans prepare organizations to quickly respond to security breaches, mitigating the impact of a breach and reducing the likelihood of long-term damage.

Discover how ECM can reduce costs, improve customer service and minimize risks associated with compliance and other challenges.
This requires careful planning, execution and continuous monitoring. Here’s how:
Find out the specific information needs and security requirements for your organization by identifying the sensitive data, critical content and documents you need to protect.
Understand regulatory requirements and industry standards you are subject to and identify relevant features required for compliance.
Look for providers with a strong security track record and certifications like ISO 27001 or SOC 2.
Ensure the vendors offer the specific security features your organization needs.
Plan for document retention and records management schedules, policies and features to keep documents secure.
Effective IG policies will help ensure data availability and business continuity.

Enterprise content management is a core business technology that helps organizations, no matter their size or industry, to organize, manage and distribute unstructured content.
Put security at its core, including detailed configuration plans for required features.
Ensure your ECM system architecture includes multiple security layers like firewalls, MFA, VPNs and RBAC.
Start your system installation by following your implementation plan to install and configure your chosen solution.
Implement security measures like encryption protocols, access control measures, audit trails and others as needed.
Verify that all security configurations are working as expected. Perform rigorous testing for system load, possible errors and performance issues.
Conduct penetration testing to simulate system intrusions and vulnerability assessments to identify and address any potential security weaknesses.
Ensure your new ECM system has all the needed security protocols in place before going live. Launch your new system with all the chosen features.
Monitor your roll-out for security incidents or areas for improvement.

Discover how you can develop an ECM strategy to implement new ECM solution to meet the current needs of your organization and prepare for future business success.
Keeping your ECM system secure isn’t a one-time effort as security threats evolve. It needs a proactive approach, requiring:
Schedule security audits regularly to identify any issues and stay ahead of potential threats.
Apply software patches and updates to fix known vulnerabilities as cyberattacks often exploit outdated systems.
Run compliance checks to stay in line with legal standards and best practices.
Implement access controls like RBAC paired with MFA to guard against unauthorized access.
Use strong encryption to secure data so it remains unreadable without the decryption key if intercepted.
Implement audit trails with detailed logging of user activities to detect and address suspicious activities.
Configure policies and settings to meet regulatory requirements and ensure critical business documents are protected from unauthorized access or changes.
Update incident response plans and hold drills to respond quickly and effectively to security breaches.
Conducting regular security training on common cyber threats keeps employees informed, reduces risks of human error and helps maintain a strong security posture.
Most automated ECM capabilities can work without end-user intervention or specialized training, but system usage and security training are still needed, especially if there are manual security or governance tasks.
Real-time monitoring can detect and identify unusual activities and flag potential breaches, enabling faster responses.
Establish a feedback loop from security incidents to learn from them and enhance your existing protocols and processes.
Be adaptable and flexible to address new challenges and adopt advanced technologies to remain effective.
Foster collaboration between IT, incident response teams and other departments to cultivate security awareness and share responsibility for ECM security across the organization.

Explore Gartner’s analysis of 15 vendors in the document management space, and see why Hyland was named a Challenger with strengths in our scalability, open source and industry-specific capabilities.
Here’s how organizations have successfully protected their content with secure ECM systems.
A property and casualty insurance company improved its document management by adopting Hyland's OnBase platform.
Consolidating multiple legacy systems into a secure, centralized repository streamlined their claims and underwriting processes. This reduced processing times from two days to 20 minutes and cut costs by over $1.5 million annually.
OnBase’s seamless integration with Guidewire ClaimCenter and its scalability support future expansions, enhancing information accessibility, processing speed and operational efficiency.
> Learn more | Property and casualty insurance company case study
Naviant, a leading ECM and BPM solutions provider, used Hyland’s ShareBase to streamline its human resources onboarding process.
To address inefficient paper-based document submission, Naviant leveraged ShareBase to create secure, web-based folders and allow new hires secure access to review and submit necessary forms.
This eliminated the paperwork, improving information security and engagement of the hiring process.
> Learn more | Naviant case study
Lantik, S.A., the public information services society for Spain’s Bizkaia Provincial Council, faced inefficiencies with three separate document repositories used by different applications.
Using Hyland's Alfresco Platform, Lantik partnered with Varios to consolidate over a million documents into a single, secure repository.
This transition has led to over 50% annual cost savings and boosted productivity for over 10,000 users managing more than 100 million documents.
> Learn more | Lantik S.A. case study
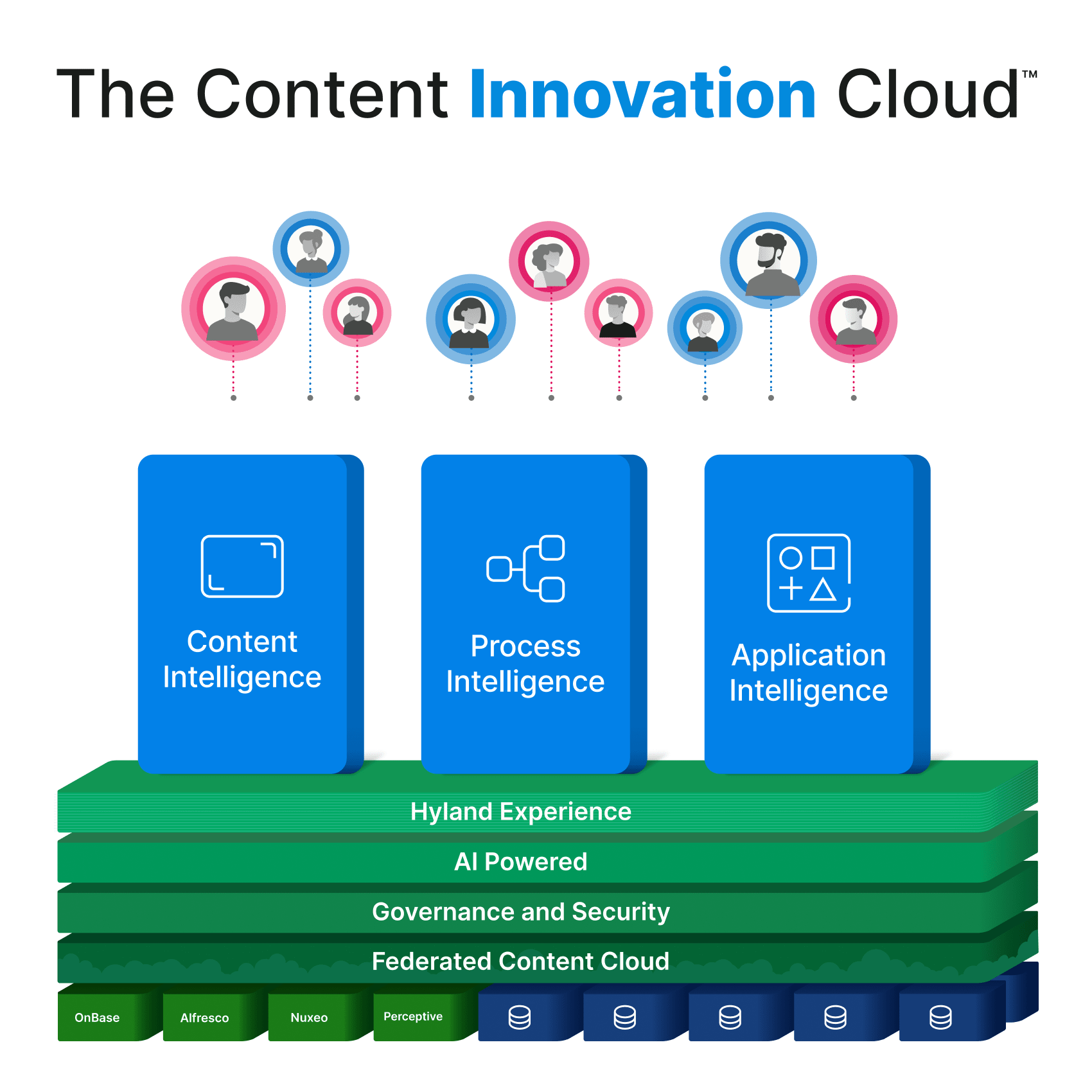
Hyland’s modern, intelligent platforms give your teams the tools they need to deliver their best today, while empowering them to innovate and adapt for the opportunities of tomorrow.
As cyberattacks become more sophisticated, organizations are focusing on advanced threat detection and response capabilities.
As new risks and threats appear, businesses are turning to:
Modern ECM systems leverage cloud-based repositories to secure content.
Contrary to perception, cloud storage is resilient to security risks, with reputable providers offering robust, multilayered security features such as:

Explore the evolution of enterprise content management and how modern ECM solutions enhance efficiency, collaboration and compliance for organizations.
ECM security is poised for transformative changes driven by technological advancements such as:
As businesses continue to embrace modernization, the importance of robust content security cannot be overstated.
ECM systems provide a comprehensive solution that addresses the complexities of protecting digital assets in a rapidly evolving technological environment.
Invest in a robust ECM system now to safeguard your content and future-proof your organization for long-term business success.

Unlock the power of efficient content management with our guide to DAM vs CMS and learn how these solutions can streamline workflows for optimal productivity.

A guide for streamlining your DAM process, from organizing and securing digital content effectively to advanced practices for facilitating efficient workflows.

Cloud technology removes barriers that organizations historically relied upon physical office environments to overcome — including security, collaboration and a sense of culture.

Cloud security is top of mind for most organizations leveraging cloud computing. The concept is simple, but the execution is complex and everchanging. Most importantly, the risks/rewards can be immense and long-lasting.